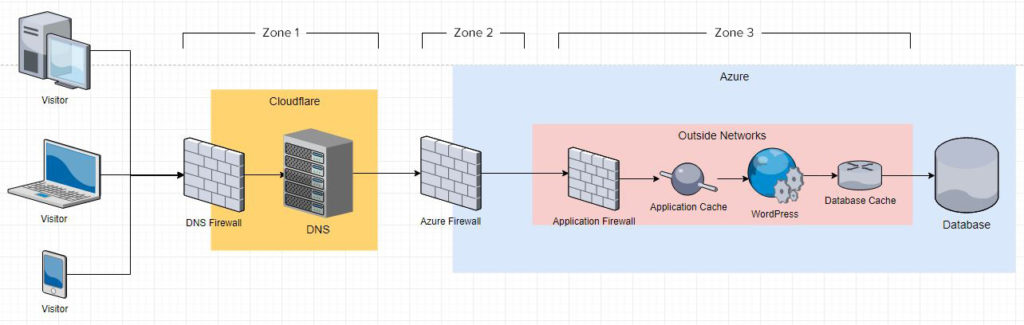
The purpose of this document is to identify and compartmentalize areas of where the web traffic flows from the consumer (which can be a visitor, piece of software, or another server) all the way to the database, the source of most data. In the environment of a WordPress Multisite in Azure, I have identified three major zones that can be hardened independently from each other but combined to enhance security. The security focus revolves around the identification and mitigation of DDoS attacks and vulnerability scanner bots.
Zone 1 – Zone 1 is the first line of defense. This zone encompasses security measurements on traffic prior to reaching the server. The two types of protection that can set up at this level is DDoS Filtering and a Website Firewall (WAF).
Cloudflare DNS is the best free option that has un-metered mitigation against volumetric DDoS. Volumetric DDoS is the most common (65% of all DDoS attacks) which involves sending a large amount of traffic (via a request) to a target that inherently saturates the bandwidth and brings the target to a crawl when performing services to legitimate users.
https://www.calyptix.com/top-threats/ddos-attacks-101-types-targets-motivations/
The free option will not stop bad bots from crawling the site. For that, you’ll need a web application firewall (WAF). Cloudflare’s WAF is in the PRO plan for $20/month and above and enterprise in the thousands.
This plan does not protect against Layer 3, 4, & 7 DDoS attacks.
What are the layers? https://www.cloudflare.com/learning/ddos/what-is-layer-7/
With those types of attack, you’ll need a WAF. Cloudflare’s WAF is in the PRO plan for $20/month and above and enterprise in the thousands. However, I found better reviews for Sucuri’s WAF starting at $9.99. https://sucuri.net/website-firewall/.
What I really like about Cloudflare other than the fact that it is free is that it has some caching functionalities and features to speed up your website. Here are some highlights. Again, these are all free!
Under Attack Mode is active
Under Attack mode is used when a website is under a DDoS attack. All visitors will be shown an interstitial page for five seconds.
Browser Cache Expiration
Determine the length of time Cloudflare instructs a visitor’s browser to cache files. During this period, the browser loads the files from its local cache, speeding up page loads.
Always Online™
If your server goes down, Cloudflare will serve your website’s static pages from our cache.
Auto Minify
Reduce the file size of the source code on your website.
AMP Real URL
Display your site’s actual URL on your AMP pages, instead of the traditional Google AMP cache URL.
Brotli
Speed up page load times for your visitor’s HTTPS traffic by applying Brotli compression.
Rocket Loader™
Improve the paint time for pages that include JavaScript.
Mobile Redirect
Redirect visitors that are using mobile devices to a mobile-optimized website.
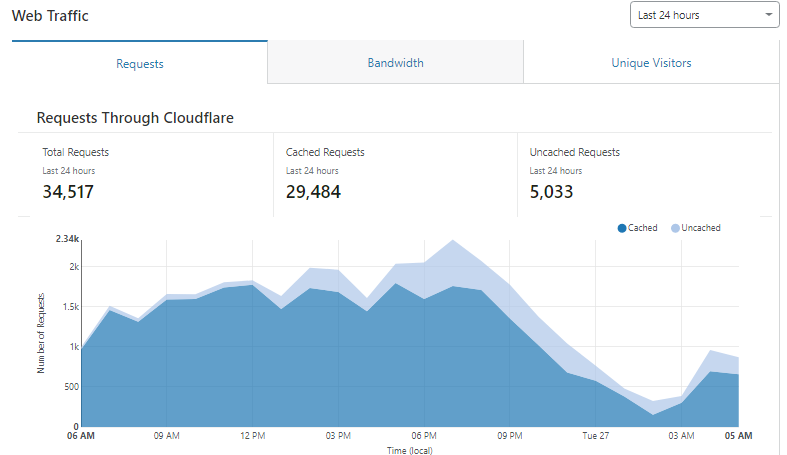
It also provides some analytics, which is nice to see how much traffic is served cached versus live.
As well as threats.
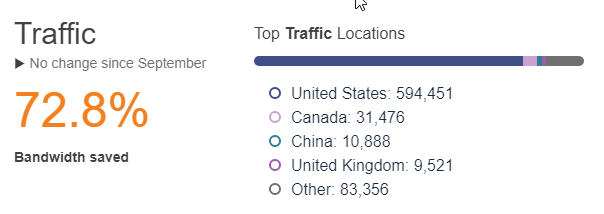
In terms of bandwidth saved alone, Cloudflare does a phenomenal job. This is the bandwidth saved on 16 client sites and keeping the hosting inodes low.
For many enterprise websites, I find the best fit to be the Website Security Platform from Sucuri for $499.99/yr. This platform includes DDoS Mitigation, WAF, and Malware scanning. The pricing plan is much clearer than Cloudflare’s. It’s one-price regardless of bandwidth and size of the website. It also has a 30-day trial period so we can test things out.
https://sucuri.net/website-security-platform/signup/
However, the top-tier Cloudflare Enterprise provides bot management which should filter out bad bots from hitting Zone 2. But the cost of the enterprise edition would be thousand per year.
Zone 2 – This is the zone where we can utilize our hosting platform to apply additional security. On the Azure platform, we can take advantage of the following security services.
- Azure Firewall
- Azure DDoS Protection
- Azure Sentinel
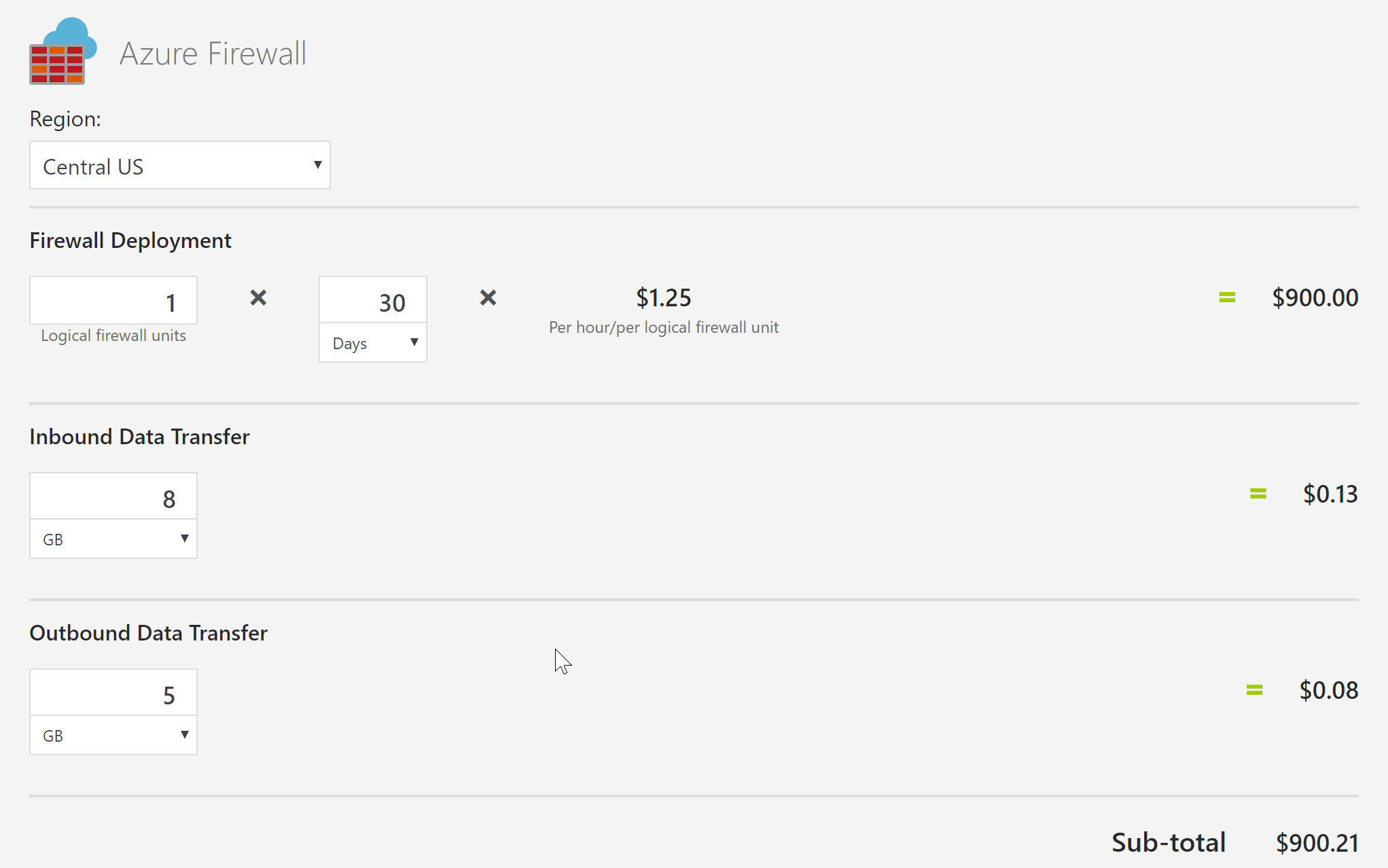
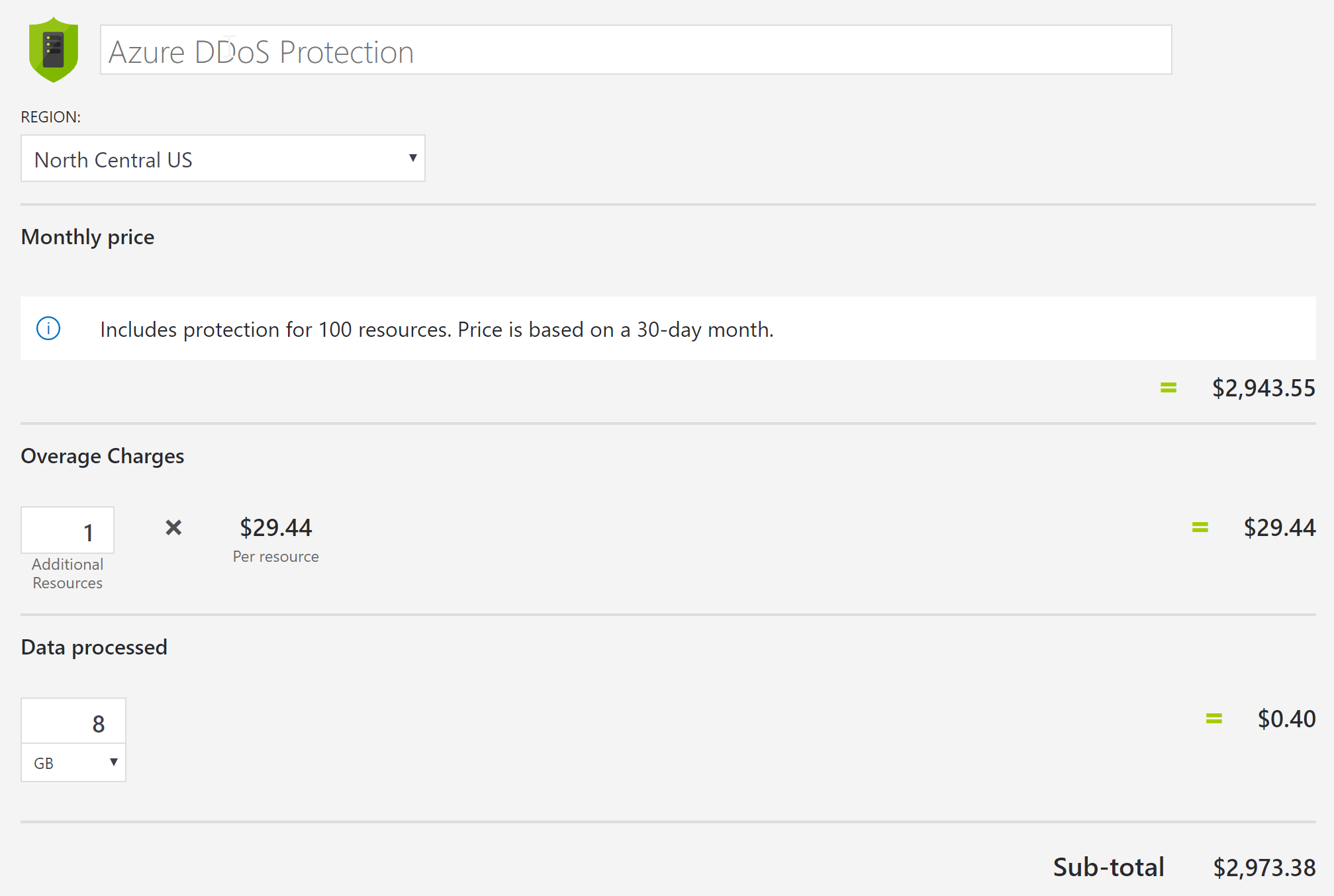
I don’t have access to Azure billing but based on some rough average estimates of 8GB in / 5GB out.
For Azure, their firewall monitors and mitigates bad traffic, but it does not prevent DDoS. https://azure.microsoft.com/en-us/services/azure-firewall/ We’ll be looking at just under $1000/month.
Azure DDoS protection also comes with a WAF which would come to $3000/month.
https://azure.microsoft.com/en-us/services/ddos-protection/
Azure does offer a SIEM, through Azure Sentinel. A SIEM will allow for better and more accurate alerts, a single command center that displays data gathered from logs produced by various systems in a way that is very readable and after its being scrutinized by machine learning and AI algorithms. This allows an admin to easily identify and take action if the system is being compromised or stabilize a breach. At this time, Azure Sentinel is only available for preview.
Zone 2 is also where we can blacklist certain IPs known to spam server. Spam IP lists can be found online.
Zone 3 – Within WordPress, there are a few plugins and security measurements that can be done to protect WordPress and the database.
WordFence is highly recommended as a WordPress Firewall if a WAF is not established in Zone 1 or Zone 2. https://www.wordfence.com/wordfence-signup/#pricing Because the firewall lives on the website itself (via WordPress), attacks can overwhelm a website versus a CDN like Sucuri or Cloudflare where it is handled before it reaches your servers. However, this offers some lines of defense at a very affordable price.
These tips should be used for additional security.
- Disable XML-RPC. This will turn off remote blog posting from other applications.
- Move the default location of the login to somewhere else. This will prevent bots from trying to brute force and take away server resources used to check credentials. A 404 for website.com/wp-admin takes a lot less processing power than having to serve a page and checking credentials entered by a bot. This is easily done with iThemes Security. https://ithemes.com/tutorials/ithemes-security-hide-login-setting-overview/
- Extra : Run a database optimization scripts https://www.cloudways.com/blog/wordpress-database-optimization-guide/
- Use sFTP whenever it is possible if your host has provided you those options.
- Use Automated Update, the one I like is https://wordpress.org/plugins/companion-auto-update/, which allows you to whitelist/blacklist certain plugins for auto-updating, as well as toggling major core updates. An email summarizing the updates can be set to send to your inbox whenever updates are made.
- Good for SEO, but great for security. Most hosts should provide some sort of free SSL certificate. Typically, they are served by Let’s Encrypt. They are typically DV SSL, so if you handle sensitive data such as credit cards, you will want to purchase an OV or EV SSL. Learn more about these different types of SSL here https://opensrs.com/blog/2015/05/dv-ov-or-ev-how-to-offer-the-right-ssl-certificate/.
One thing I also like to do is manually blacklist certain IP addresses that have been found to spam my server. This feature depends on your host. It can be located in the cPanel.