So this is a quick copy-pasta recipe to removing TLS 1.0 / 1.1 from your Linux server that also has Let’s Encrypt SSL. Removing TLS 1.0 and 1.1 is vital for ensuring security for your servers. You will not get above a C rating on SSL Labs without it being turned off.
Some quick links for additional info.
- https://geekflare.com/enable-tls-1-3/
- https://serverfault.com/questions/848177/how-can-i-disable-tls-1-0-and-1-1-in-apache
- https://www.ssl.com/guide/disable-tls-1-0-and-1-1-apache-nginx/
The first thing you’ll need to do is quickly assess to see if you even have TLS 1.0 and 1.1 turned on. I use this tool for a quick lookup. If it says TLS 1.0 and 1.1 is enabled, then you can proceed to disable them.
SSH into your Linux server and put in this command.
sudo nano /etc/apache2/mods-available/ssl.conf
And then look for something like:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-P$......
and you’ll want to comment it out and replace it with:
SSLCipherSuite "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384"SSLProtocol TLSv1.2
Save it and let’s move on. Put in the following command:
sudo nano /etc/letsencrypt/options-ssl-apache.conf
And look for this line:
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM$......
comment it out and replace it with:
SSLProtocol +all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-EC$
Save it. I wanted to remove some of the suites that SSLab was warning me on, but if you want the whole suite, you can use
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-EC$
The last thing that that needs to be done is reboot Apache for the changes to take place.
sudo service apache2 restart
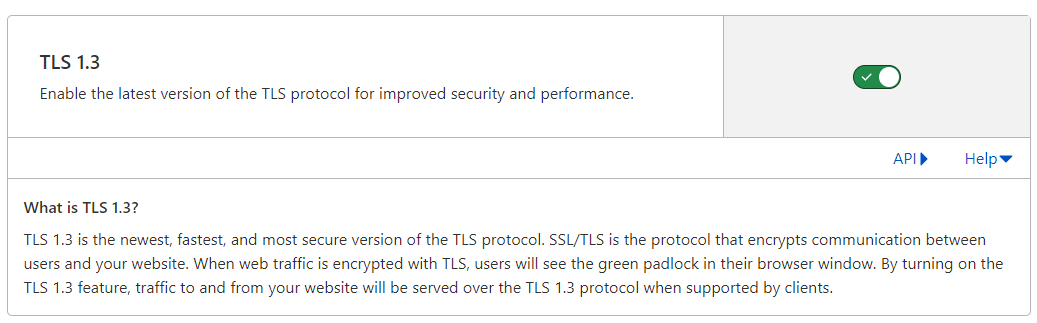
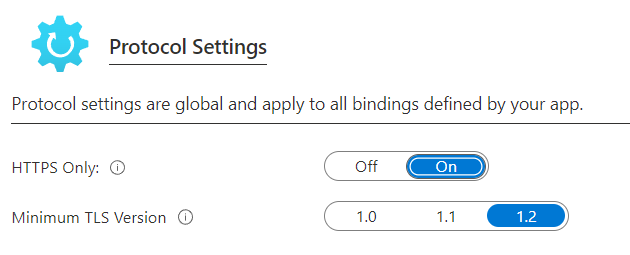
And then you would just double-check your work via the quick lookup tool and SSL Lab. For me, removing TLS 1.0 and 1.1 didn’t break anything on my website. SQLSRV appears to be working without any issues. All images and content loaded without a problem on all the major browsers (Chrome, Edge, Firefox, Safari). So this change should be low impact. As of this writing, TLS 1.3 isn’t a toggle switch yet for Azure App Services, but it is a toggle switch in Cloudflare.
Cloudflare TLS Options
Azure TLS Options
Comments (0)